AI/ML-Driven Open-Source Framework for Network Anomaly Detection
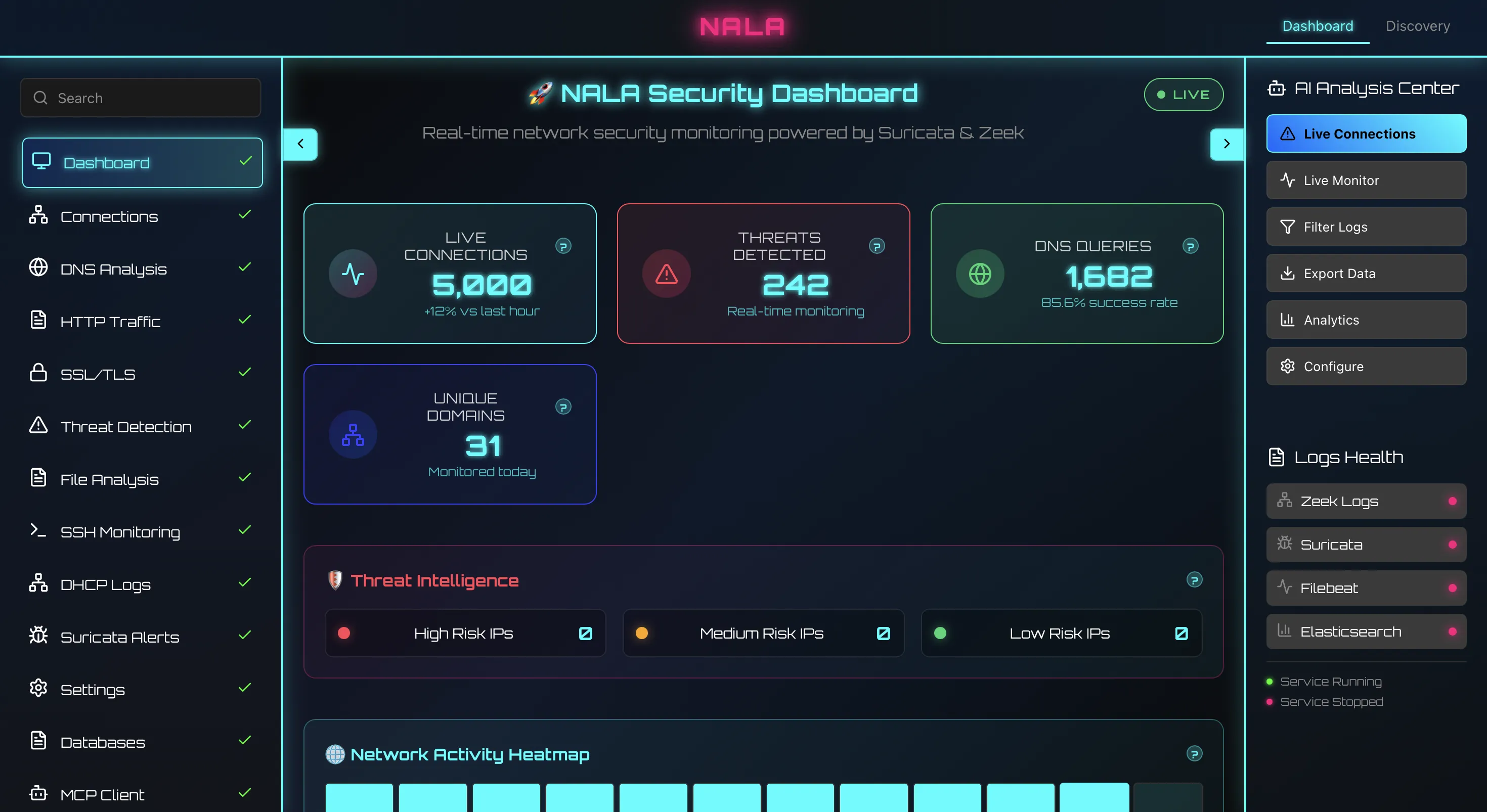
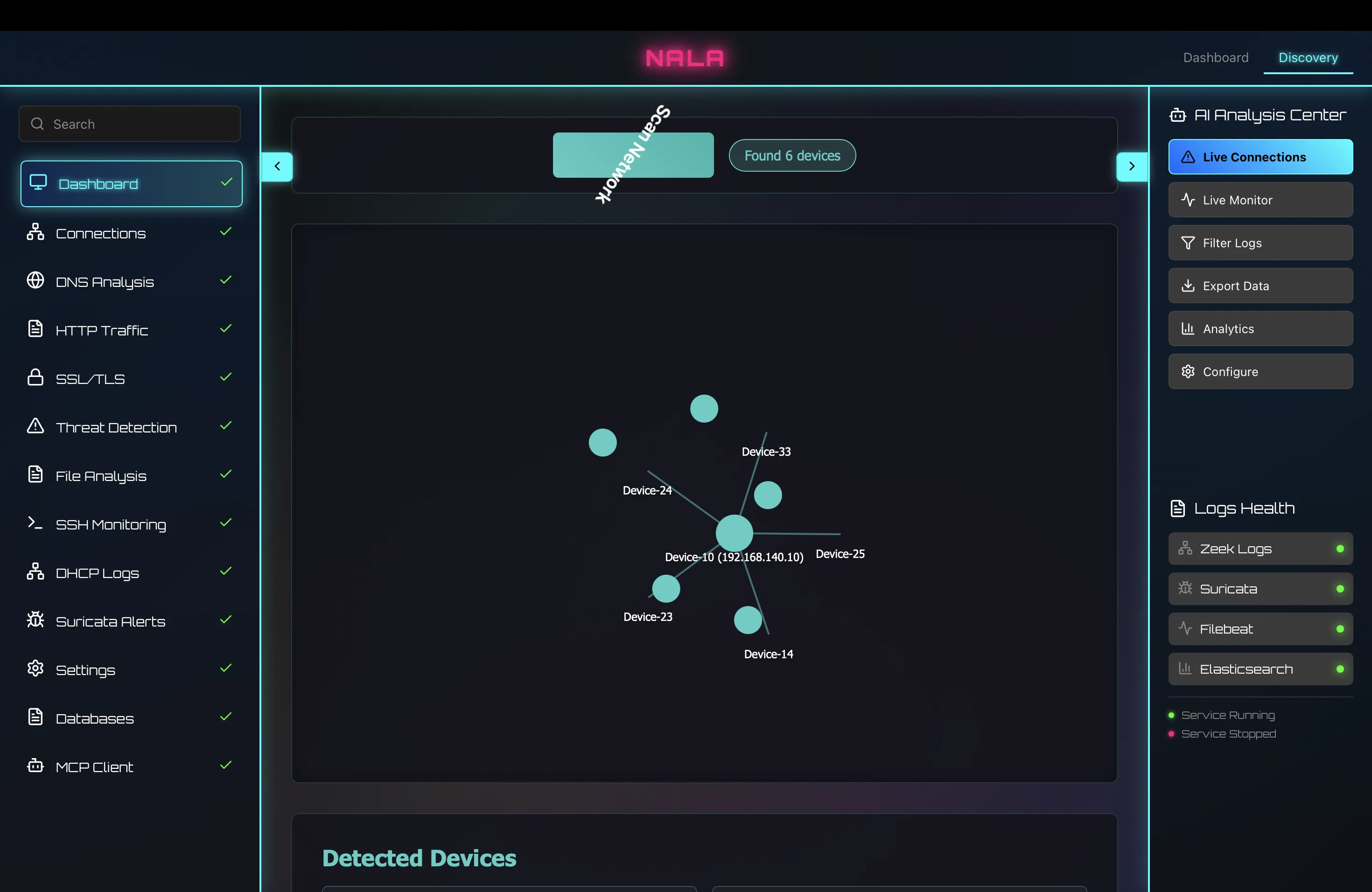
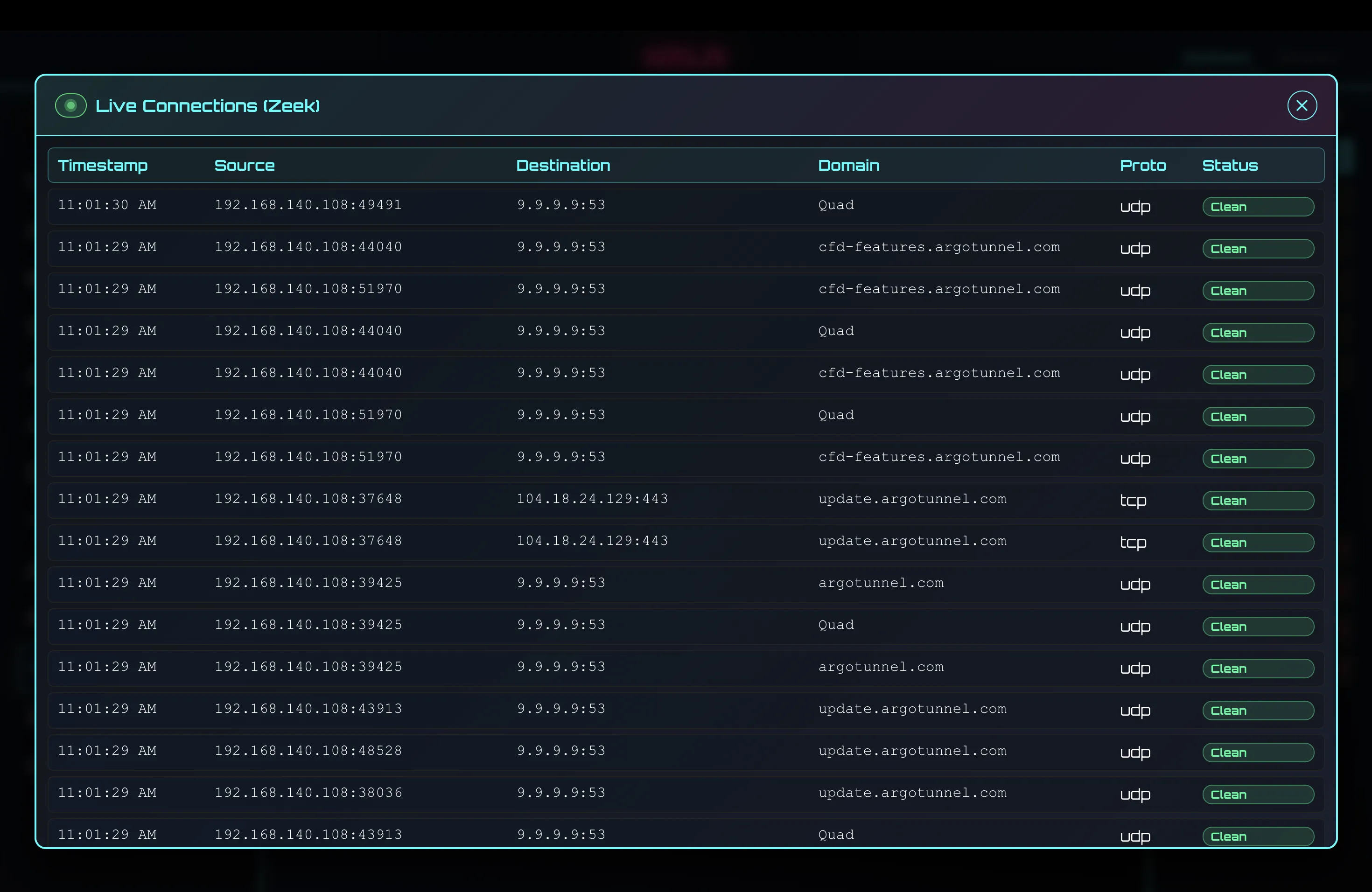
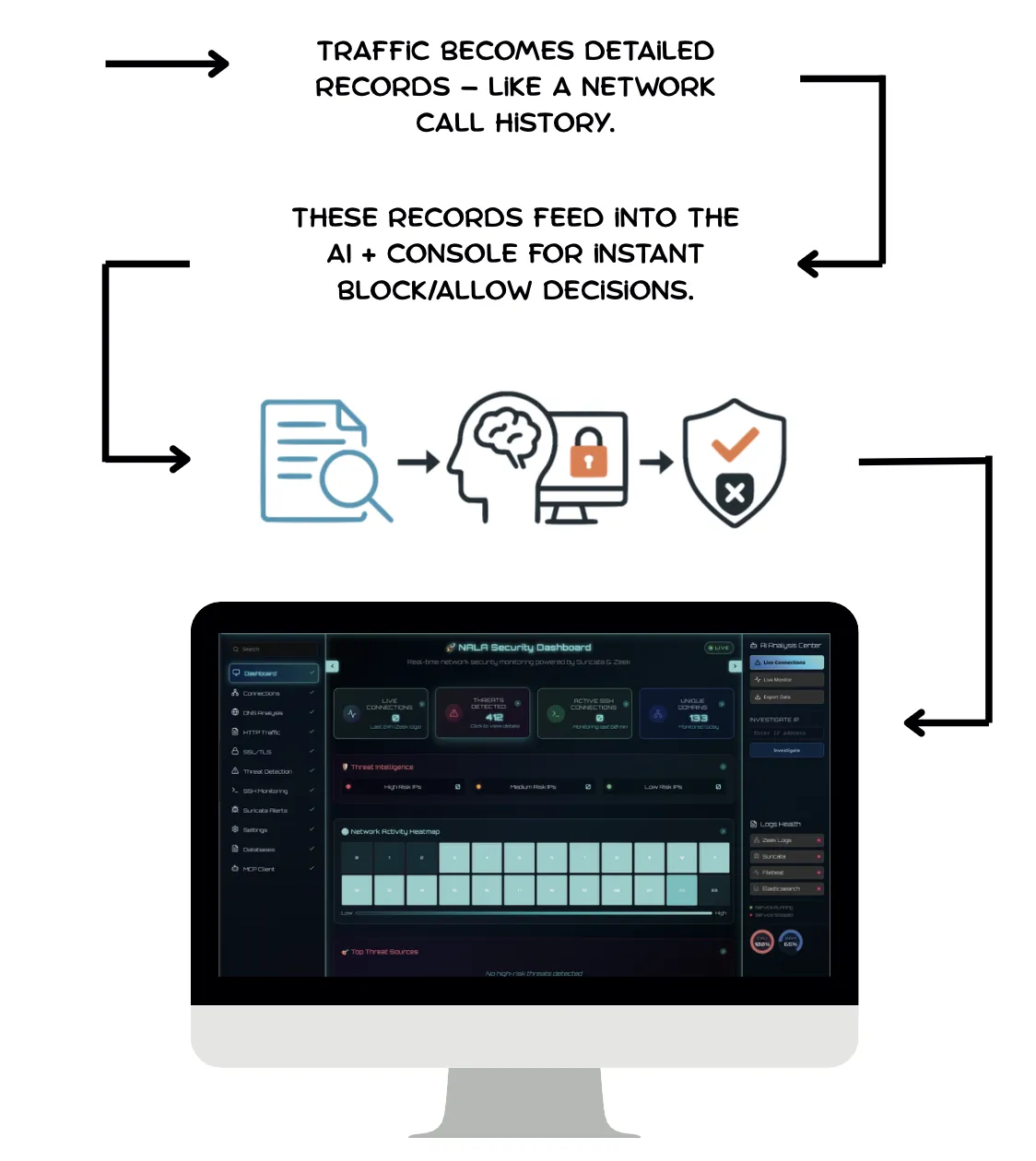
An accessible, modular alternative to traditional SIEMs that combines Zeek and Suricata for deep traffic visibility, AI/ML (Fine-Tuning + RAG) with MCP-controlled analysis for anomaly detection, and OPNsense API for automated, real-time enforcement.